A Complete Guide: Wallet Virus File Ransomware Removal & Recovery
Ransomware is a brand new virus that has emerged on most of the users Desktop. Many individuals become panic when all of sudden they have faced an issue of ransomware virus where all the private files are encrypted and attached with .wallet extension also. Moreover, it is commonly used for the other thousands of viruses like Locky, Gerber, Shades. The main purpose of this virus is to make the victim to pay the ransom to delete the worms. Sometimes, Ransomware virus enters directly on users PC where they have downloaded the file-encrypted program. That means users system have stuck with deceiving type of virus. First of all, it will corrupt the essential data saved in the computer such as MDF file that creates a major issue. Hence, corrupted or damaged .mdf files handle the most problematic situation get the .wallet extension just because of Dharma ransomware virus attack. So, it becomes very important for Virus file ransomware removal & recovery from the computer system. Now, we are going to discuss the methods how to Wallet Virus infected files.
Ways to Get Infected with Virus file Ransomware
For better understanding about this .wallet file extension, let us discuss this new ransomware virus attack on a local machine. It is a kind of virus, which is sent to the victim’s database directly. Especially, most of the hackers prefer this way because it is more effective and easy. Even this virus is shared through an email or message once the user has clicked on the link or open the mail. Then, the virus file ransomware directly attacks the system. Moreover, it will start scan users PC and find out the private files. After searching all of them like images, MS Office documents, videos, songs, MDF file and so on and save them using .wallet extension then, lock the data. Also, it can add .txt, .bmp and .html file to each folders that saves encrypted detail. Thus, users are unable to access because it utilizes strong encrypting ciphers and most of the users cannot read it. Multiple times, the primary target of ransomware is to attack the necessary files, which are stored on the Desktop such as .mdf file and easily forced a user to give the ransom. Thus, to overcome this situation, users need some solutions that are covered in this article.
Manual Methods to Recover Ransomware Files
Solution 1: Delete .wallet Extension
There are various steps given below that helps a user to remove the Wallet ransomware virus and recover ransomware files:
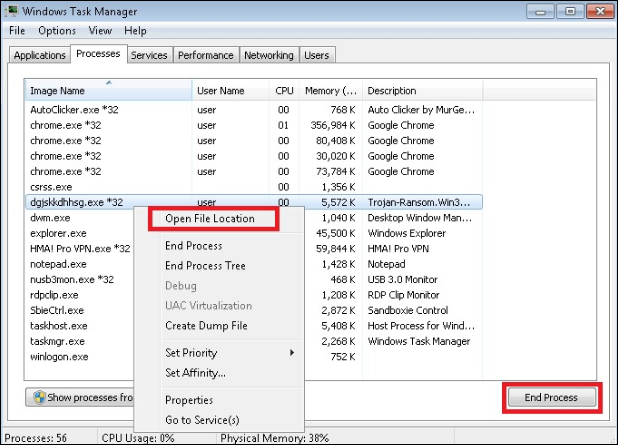
Step 1: Using Task Manager
- First, click Ctrl+Shift+ESC shortcut keys to Open the task manager on your machine.
- Now, trace the process of ransomware. Make sure it is a randomly generated file.
- Now, trace the process of ransomware. Make sure it is a randomly generated file.
- Before killing the process, enter the name on the text document for further purpose.
- After that, go to the suspicious procedure, which has the .wallet extension encryption virus.
- Right-click on the process and then, open the desired location of the file.
- Next, click on end process and delete the suspicious files directories.
Finally, can be possible that procedure is hidden or difficult to detect.
Step 2: Detect the Hidden Files
- Open the folder as per your choice and then, select organize option.
- Now, choose the folder and search option.
- After that, click on view tab >> select an option of hidden files and folders.
- Now, uncheck the Hide protected operating system files option.
- Once it is unmarked then, click on apply option and press OK button.
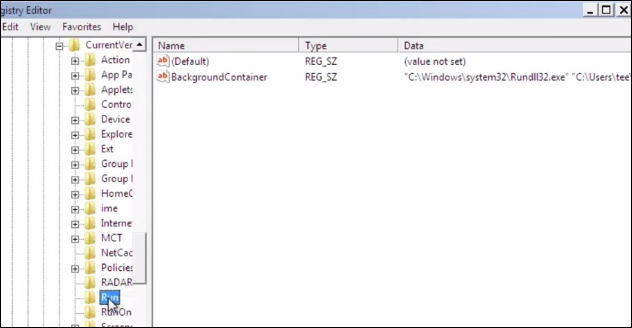
Step 3: Go to the Location of Startup
- Once the OS loads properly then, press Windows logo+ R key from the keyboard.
- Now, a dialog box will display and type “Regedit” in it.
Remember: Be careful while editing the MS Windows registry as it might render the system gets broken.
Next, depending upon the OS that are used, follow below path:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run] .
After that, remove the Display name.
- Then, open the Explorer and go to:
%appdata% folder and remove the executable.
- Using such steps, a user may be able to delete the .wallet ransomware manually from any type of file like MDF file. However, if it is still present, then, go for the second solution given below.
Solution 2: Recover Encrypted Files
The best solution for restoring the data from a recent backup, in that case, the users have one.
By Using Third Party SQL Recovery
In case, if a user unable to have the backup of the MDF file then, he can go for an alternate solution i.e. SQL Recovery to recover corrupted MDF database file. It is an amazing application that is designed specially to recover the data from corrupt MDF database file completely in the safe and secure way. It is the best software that will beneficial to remove wallet virus file ransomware from MDF data file.
To recover encrypt files, download rename the data file with the .mdf format. Once it is renamed then, follow the mentioned steps:
Step 1: Firstly, install and launch the software on your machine.
Step 2: Now, choose the open option to browse the MDF file from the stored location.
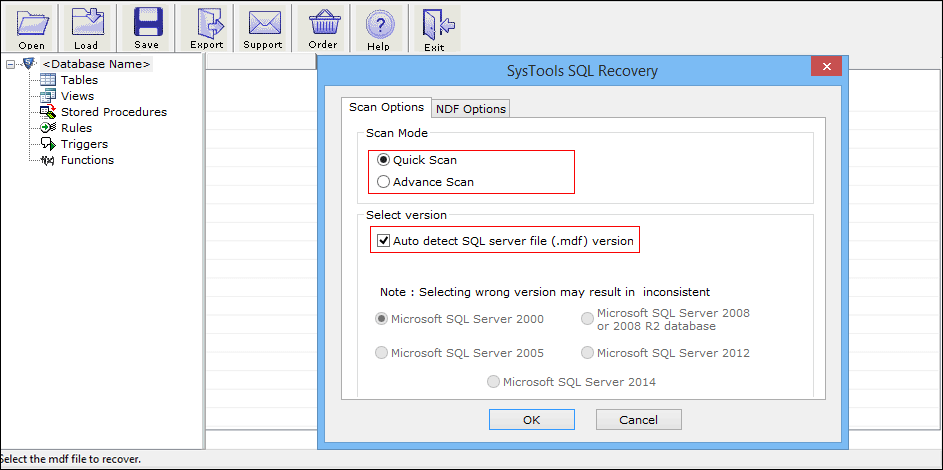
Step 3: After that, decide the mode of scanning the data file and choose the version of SQL Server by selecting the desired option. Once the file is recovered or restored the application will display the recovery message on the screen.
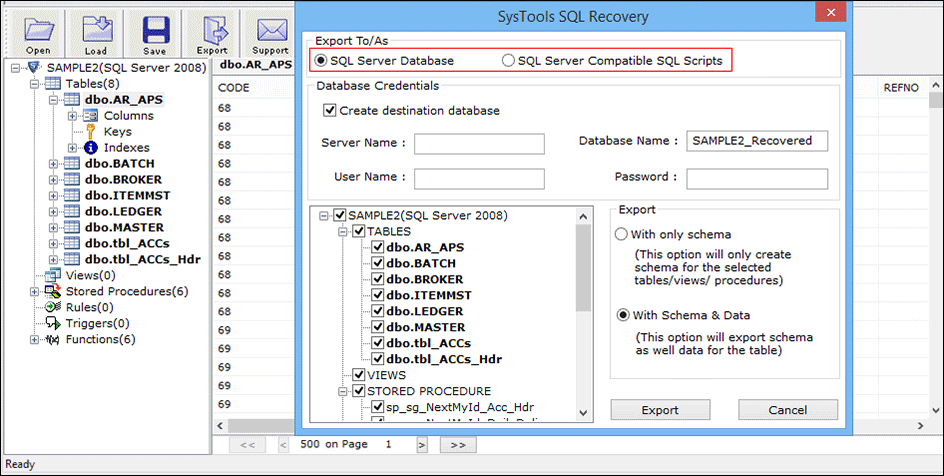
Step 4: Next, the utility provides an option for exporting the recovered data to the desired place accordingly. Then, enter the database credentials to export the data.
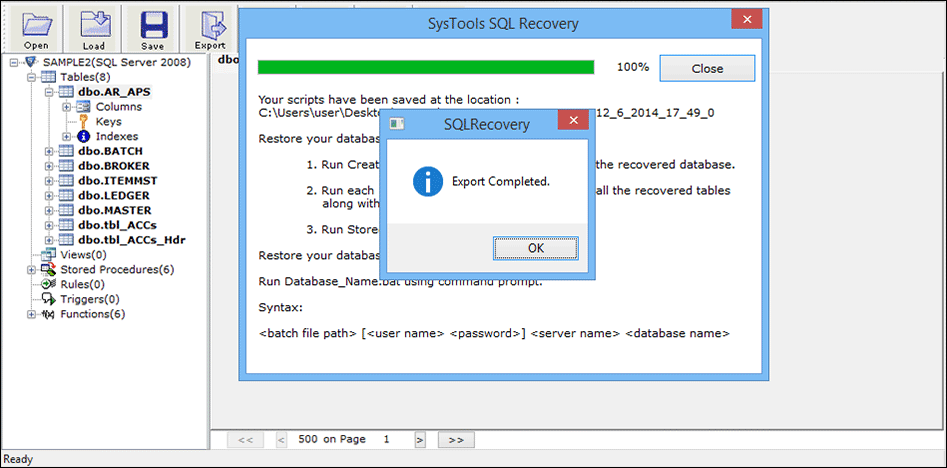
Step 5: After exporting finish, the software will show the completion message.
Conclusion
Wallet Virus file ransomware file is a type of virus that enters the user’s computer system and needs to encrypt the database file such as .mdf data file. After considering this, we have discussed different methods to restore the data from encrypted .wallet ransomware in an efficient way. Also, discussed a third party solution i.e. SQL Recovery in detail.